“Do not reinvent the wheel.” That’s the principle Mule applies when it comes to Mule Message Security. Anypoint Enterprise Security is a suite that comes bundled with all the necessary modules/methods for applying security to Mule Service Oriented Architecture (SOA) implementations and Web services.
Objectives
My main concern regarding the security was Mule Message Encryption. Mule provides three extraordinary Encryption Strategies:
- JCE Encrypter: encrypts stream, byte[] or string.
- XML Encrypter: encrypts string, encrypts individual fields using xpath expressions.
- PGP Encrypter: encrypts stream, byte[] or string. In this blog post I will try to explain how to configure Anypoint Studio for applying encryption strategies to mule messages using the JCE Encrypter.
Let's Jump Right In!
Time to get our hands dirty. We'll cover everything we can, beginning with the installation of Anypoint Enterprise Security. We'll also go over troubleshooting practices during the installation process.
Installation of Anypoint Enterprise Security
I am using Mule 3.8.2 EE for this experiment. Take a look at this link if you'd like to dive into the installation guide in detail. Here is a screenshot:
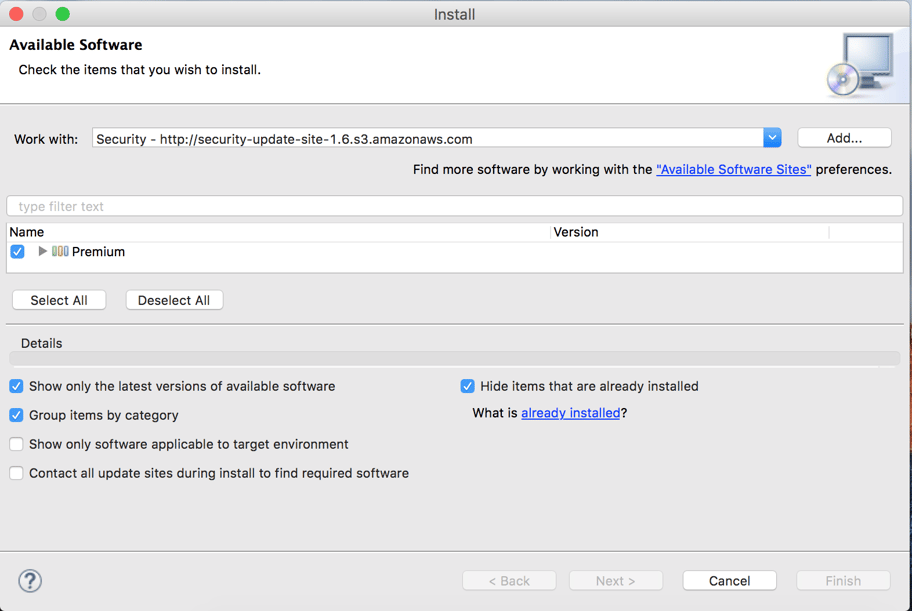
Please select the Premium bundle and proceed. In my case I could not install the software initially. If the same problem continues in your case please uncheck the “Contact all update sites during install to find required software” checkbox.
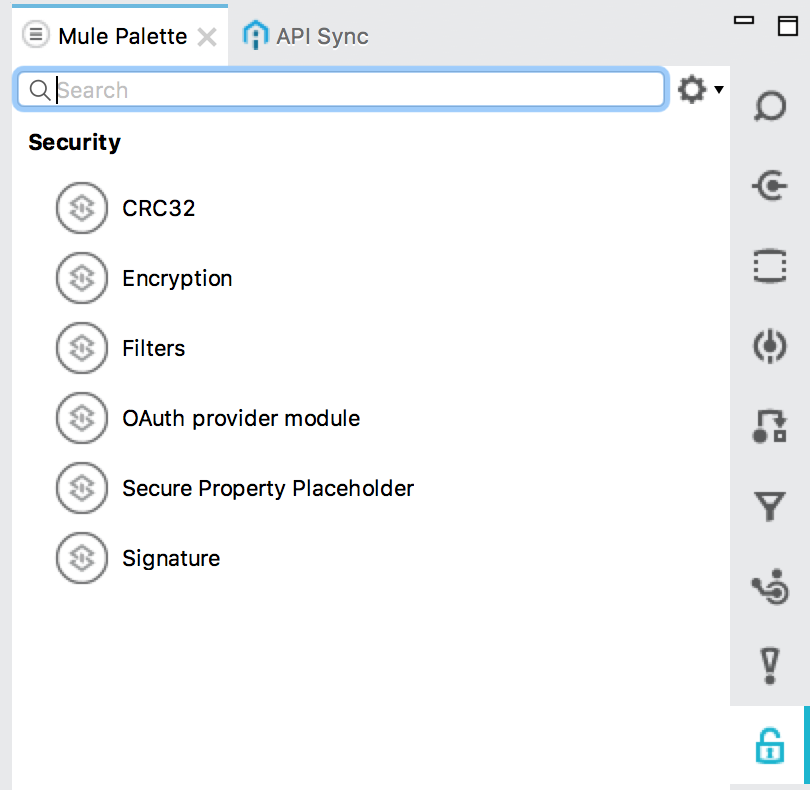
After successful installation, restart your Anypoint studio. You should see the following components under the security group palettes.
Now you are ready to go!
Creating a Mule Maven Project
Let’s create a simple Mule Maven project using Anypoint Studio. The most important point is to add the following repository in the pom.xml file.
<repository>
<id>mulesoft-public</id>
<name>MuleSoft Public Repository</name>
<url>https://repository.mulesoft.org/nexus/content/repositories/public/</url>
<layout>default</layout>
</repository>
Creating a Simple Flow
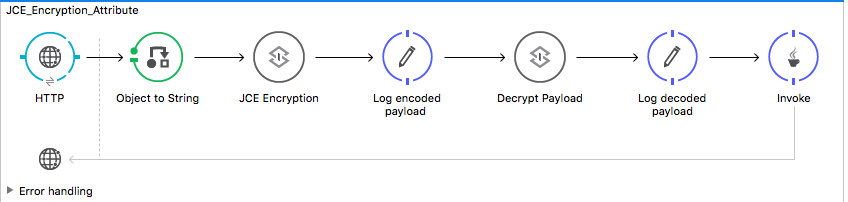
Let’s create a simple flow. The scenario is as follows: we send some JSON data to an HTTP endpoint. Then, the JSON data is encrypted using JCE Encryption Strategy, and we log the encrypted data. After that, we simply decrypt the encrypted data and log it. Here is diagram of the flow.
Digging Into JCE Encryption
“The Java Cryptography Extension (JCE) is an officially released Standard Extension to the Java Platform and part of Java Cryptography Architecture. JCE provides a framework and implementation for encryption, key generation and key agreement, and Message Authentication Code (MAC) algorithms.”
Step 1
First let’s configure a global Encryption element.
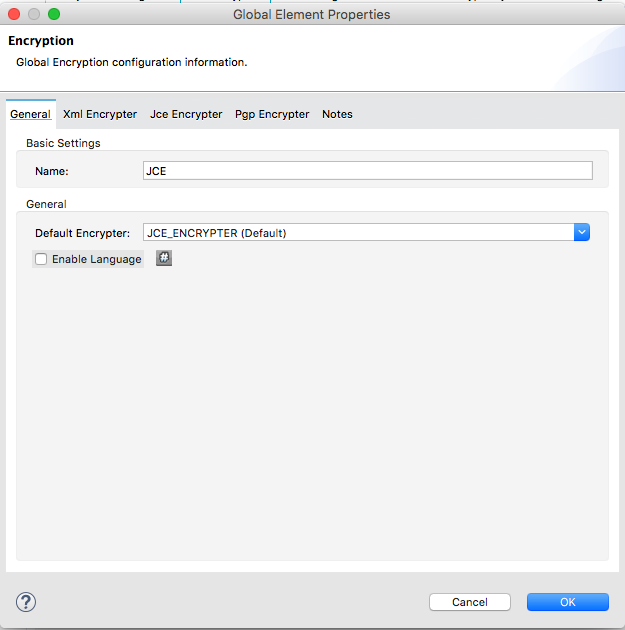
Be sure to select the Default Encryptor dropdown as JCE_ENCRYPTER. I have named the global element as JCE.
Step 2
Now, having configured the global Encryption element in step 1, we'll configure the Encryption component (labeled as JCE Encryption in the flow. This is a Encryption palette found under the Security category of Mule palettes). Here is the screen shot:
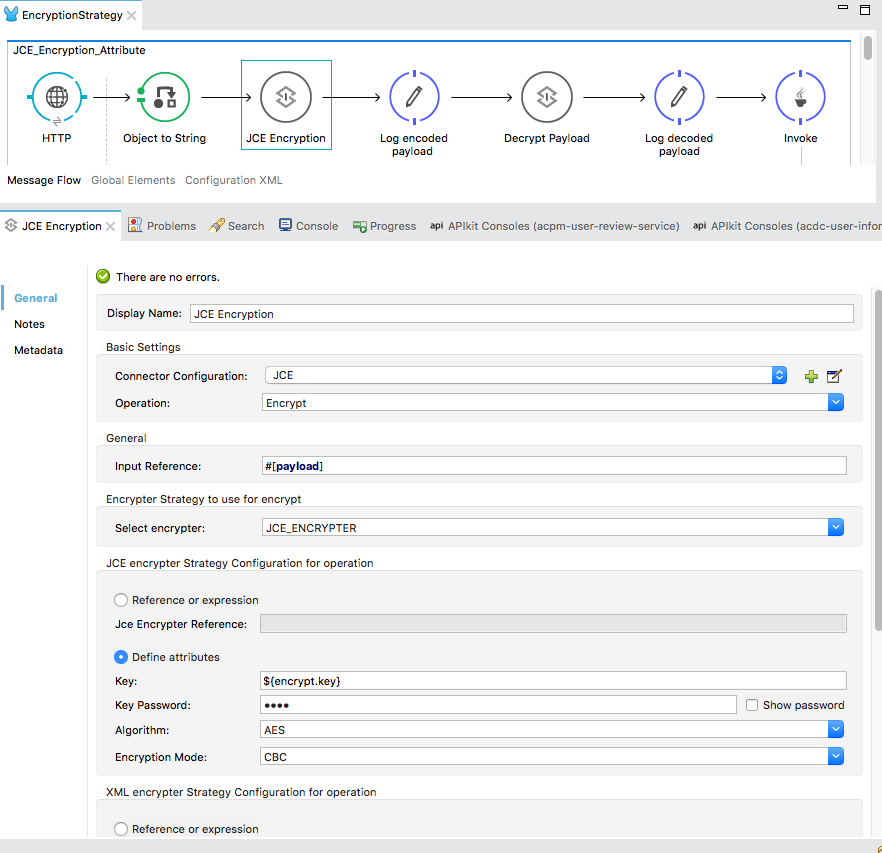
In the Connector Configuration, please select the global encryption element(JCE) that we previously defined in step 1. In the Operation dropdown, select Encrypt. In the Input Reference field, I am adding the whole payload (JSON data) for encryption. Don't forget that you can use MEL expression here to encrypt some part of the payload too. Since we are using JCE_ENCRYPTER in this example, our next step is to configure it. Select the Define attributes radio button in the JCE encrypter Strategy Configuration for operation category.
Key: Must be a 16 digit phrase.
Key Password: (whatever you wish)
Algorithm: Choose an algorithm from the dropdown list.
Encryption Mode: Choose from the dropdown list.
That’s it. You are ready to go! There is another way to make it more secure using Keystore, but that's another topic for another day.
Step 3
In step 2 we have successfully encrypted the message. Next, let’s decrypt the encrypted message. Here we are going to configure the component labelled as Decrypt payload. (This is nothing but an Encryption palette found under the Security category of Mule palettes. Here is the configuration:
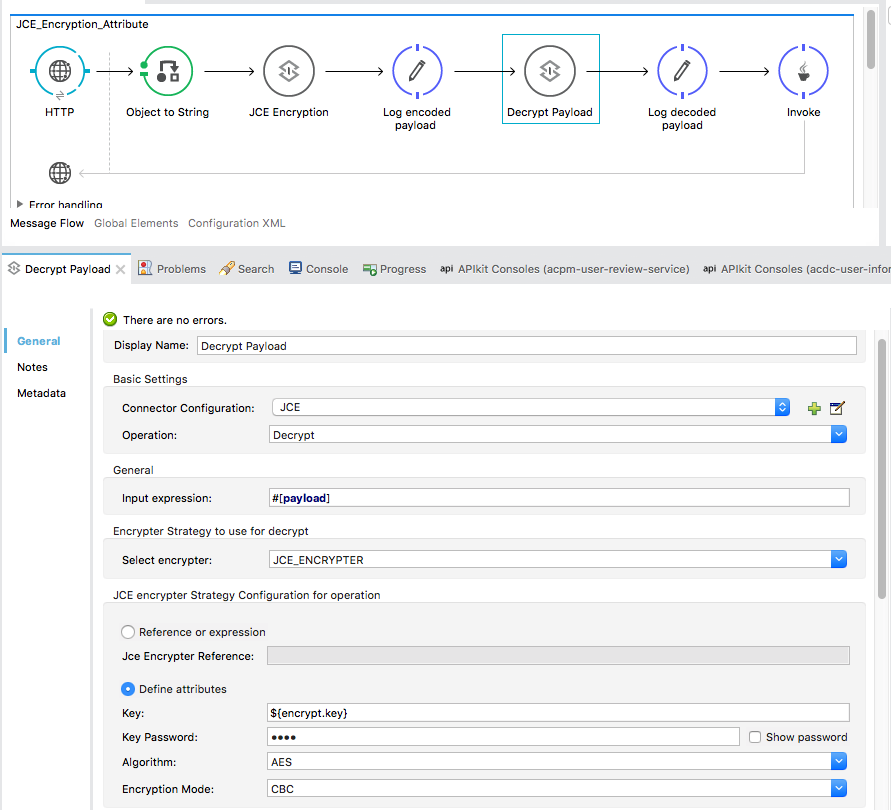
As you can see, this configuration is almost same as for encryption. The only difference is the Operation: Decrypt.
Testing
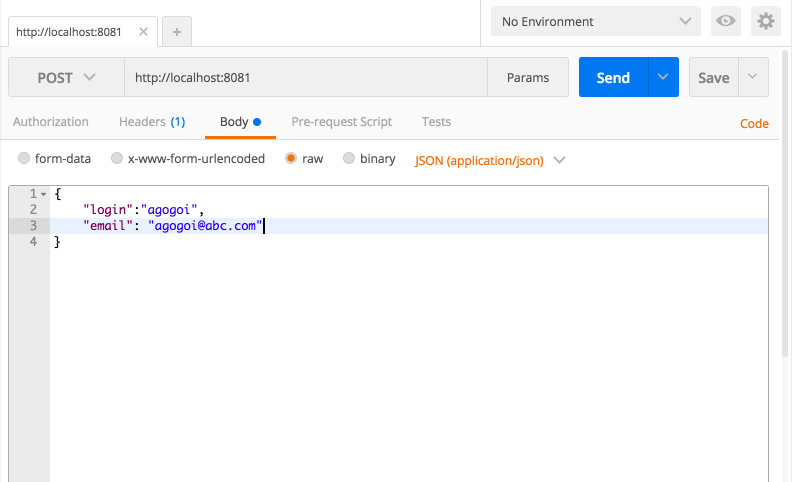
Finally, let's run the project and then send a POST request with JSON payload. I am using Postman for this operation. Observing the Anypoint console, you can see the encrypted message as well as decrypted message.
Source code can be found here.
Final note: You can use mvn eclipse:eclipse to import the maven dependencies.
Thanks for reading! Hopefully this was helpful. Any questions? Let me know in the comments!
Author
Anupam Gogoi
Anupam Gogoi is an Integration Engineer at Avenue Code. He has been working in software development for about 9 years, implementing solutions in Java technologies as well as in SOA domain. He is a hardcore JAVA and MIDDLEWARE evangelist.